Simplified Solutions delivers expertise in payment consulting, cybersecurity, and digital transformation, driving seamless growth, greater agility, and compliance with strong protection, risk management, and innovation for secure and scalable business success, focused on simplifying your enterprise.
Key Insights
Ransomware costs are surging, digital transformation is expanding with AI and IoT, and card data breaches remain a serious threat, exposing millions of records on dark and clear web platforms.
The average ransom in a ransomware attack in 2024, up by $1 million from 2023.
Digital transformation spending to hit $2.5T by 2027, driven by AI, IoT, and security.
Clear card records were posted for sale across dark and clear web platforms in 2024.
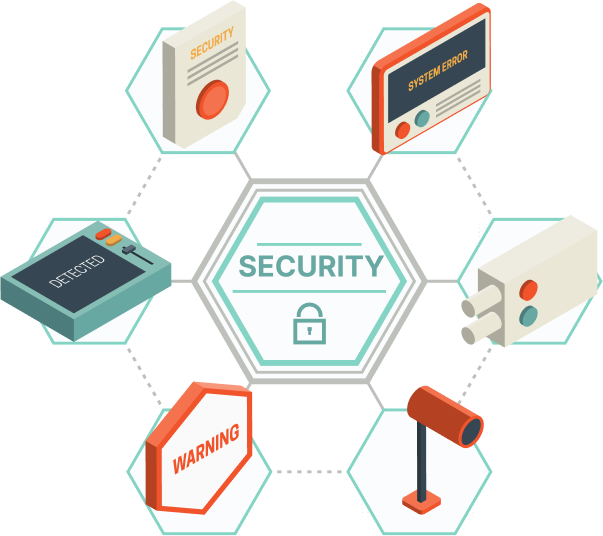
How do we safeguard your digital assets?
Regulatory & Compliance
With us on board, we assist organisations with Governance, Risk, and Compliance, preparing you for audits including PCI DSS, PCI SSF, ISO 27001, and GDPR. We handle all the heavy lifting to ensure readiness.
Offensive & Defensive Security
We ensure the application and the infrastructure follows strong security controls. We simulate sophisticated real-world attack, conduct security assessment to help you to increase security posture.
Security By
Design
Trusted By
At the forefront of technological innovation, we specialize in delivering advanced, tailor-made solutions that empower leading global brands to excel in their industries, transform their operations, and achieve unparalleled growth through cutting-edge technology and strategic expertise.