Build
Cyber Resilience
While there may not be a silver bullet for cyber resilience, partnering with Simplified Security to enhance your cyber resilience will help you transition from a reactive to a proactive approach.

DevSecOps
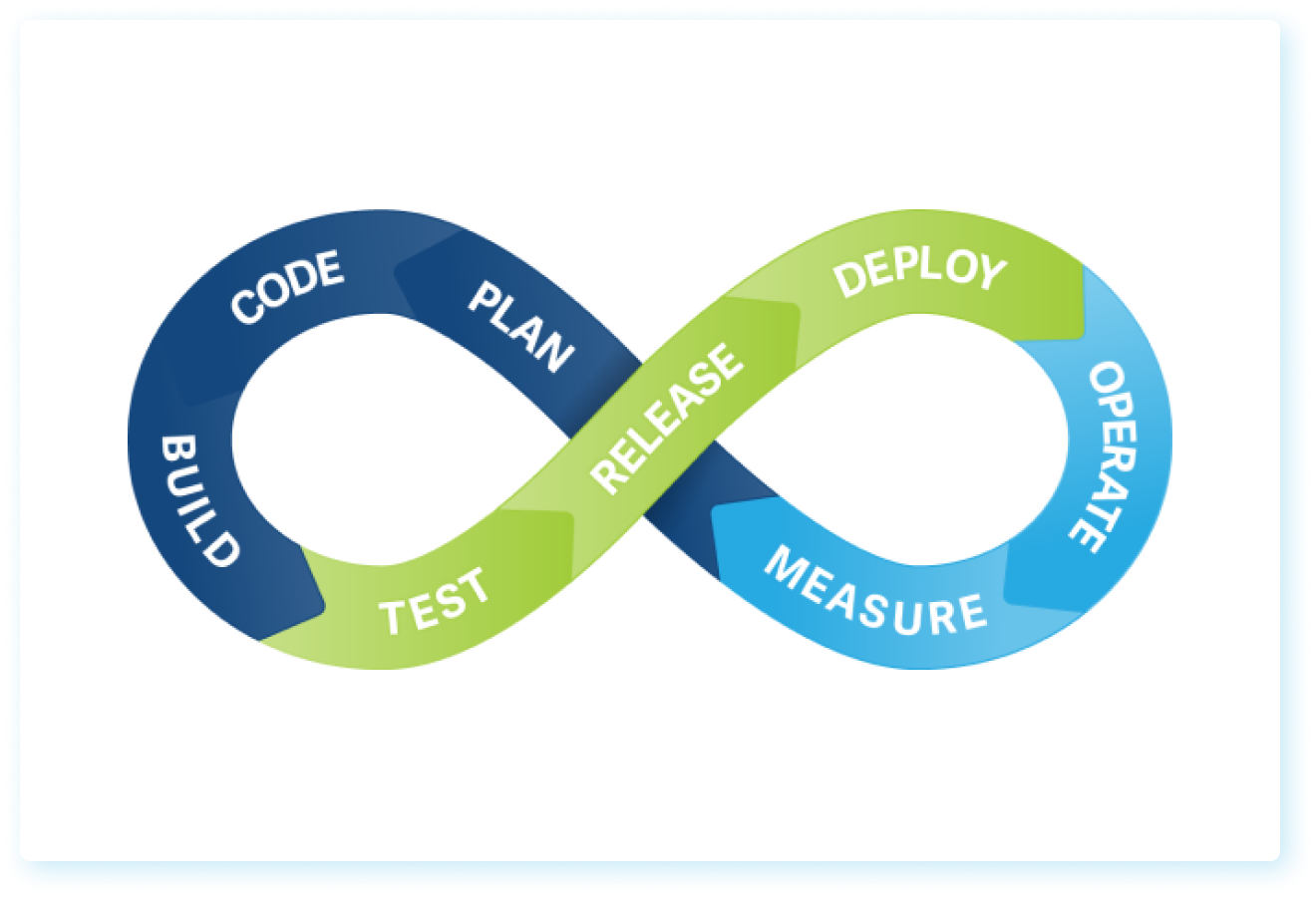
DevSecOps
What We Do?
Security Architecture
We conduct in-depth assessments of your security architecture, identifying vulnerabilities and recommending improvements. Our analysis covers network segmentation, access controls, cloud security, encryption, and identity management. We also evaluate incident response capabilities and guide the integration of emerging technologies. Our service provides actionable insights to enhance security, align with industry best practices, and ensure regulatory compliance while supporting business objectives.
Secure Code Review
Our secure code review or Static Application Security Testing (SAST) enhances the code security of your applications. Our approach includes both manual and automated code reviews to identify vulnerabilities and coding flaws. We assess security controls, data handling practices, and adherence to secure coding standards. Our team provides detailed reports highlighting issues and actionable remediation steps. By integrating secure coding practices into your development process, we help you build resilient applications that safeguard sensitive data and comply with industry regulations.
Cyber Security Strategy
Our comprehensive cyber security strategy involves assessing risks, threat modeling, and developing policies, standards and procedures to protect against vulnerabilities. Strategy is tailored to your organisation’s risk appetite. Strategy will incorporate penetration testing, and vulnerability assessments are used to identify and address weaknesses. Identity and Access Management (IAM) secures user authentication, while Endpoint Detection and Response (EDR) safeguards devices. Business Continuity Planning (BCP) and Disaster Recovery (DR) ensure operational resilience. Examples include securing cloud infrastructure with Zero Trust models and conducting phishing simulations to enhance security posture.
Risk Management and Governance
Our Risk Management services include identifying, analyzing, treating, and monitoring risks, through asset inventory, vulnerability assessments, implementing controls, and continuous monitoring. Our Governance services focus on aligning security with your business goals, developing robust policies, ensuring compliance, and establishing decision-making frameworks. We also help build a strong security culture and drive continuous improvement.
Business Continuity & Disaster Recovery (BC/DR)
Our tailored Business Continuity & Disaster Recovery (BC/DR) services to ensure resilience against disruptions. We provide risk assessments, backup and recovery planning, high-availability solutions, and disaster recovery strategies. Our services include crisis management, incident response, and regular DR testing to minimize downtime. With effective failover mechanisms and real-time monitoring, we help businesses safeguard critical data, maintain operations, and recover swiftly from cyber incidents or unforeseen disruptions.
Security Awareness & Training
Our security Awareness and Training services to strengthens your organisation’s defense against cyber threats. We provide training on cyber hygiene, phishing awareness, secure coding practices, and compliance requirements like GDPR and PCI DSS. Our programs include simulated phishing exercises, hands-on secure development training, and executive-level cybersecurity awareness. By educating employees on threat identification and best practices, we help organizations reduce risks, enhance security culture, and ensure regulatory compliance.
Compliance & Regulatory Support
Compliance & Regulatory services help businesses meet industry standards like GDPR, ISO 27001, PCI DSS, NIST, and SOC 2. Our services include security audits, gap analysis, and readiness assessments to identify compliance risks. We also offer vendor and third-party risk management to ensure supply chain security. By aligning security controls with regulatory requirements, we help organizations achieve compliance, reduce risks, and maintain trust with customers and stakeholders.
Privacy By Design
Privacy by Design Services integrates privacy protection into your organization’s foundation. We conduct privacy impact assessments, implement data minimisation strategies, and design user-focused privacy controls. Our approach includes end-to-end security measures, privacy-preserving data architectures, and clear, transparent policies supported by advanced technologies. We also establish strong data retention and deletion protocols, provide staff training on best practices, and conduct regular audits to ensure ongoing compliance with evolving regulations.
Security By Design
We embed security early in the software development lifecycle, minimising vulnerabilities while aligning with IT and business objectives. Our services include threat modelling, architecture and design reviews, and vulnerability assessments. By incorporating industry security standards, we strengthen application security from design to deployment. We help businesses integrate security into DevOps tools and workflows, automating compliance through Continuous Delivery (CD). Our solutions include static code analysis, dynamic vulnerability scanning, and third-party security tool integration in CI/CD pipelines.
Red Team, Blue Team
Our Red Team and Blue Team exercise offers a comprehensive approach to cybersecurity. The Red Team simulates real-world cyberattacks to identify vulnerabilities, while the Blue Team focuses on detecting, responding to, and mitigating threats. Key activities include penetration testing, threat hunting, incident response drills, and evaluating security controls. This collaborative exercise enhances detection capabilities and improves response strategies. Our service provides actionable insights to strengthen your defenses, ensuring resilience against evolving cyber threats and safeguarding critical assets.
Penetration Testing and Vulnerability Assessment
Our expert team conducts Penetration Testing and Vulnerability Assessments to identify weaknesses in your infrastructure, applications, and processes. We simulate real-world cyberattacks through thorough scans and manual testing, assessing the potential impact of discovered vulnerabilities. Key activities include network penetration testing, web application assessments, social engineering simulations, and cloud infrastructure evaluations. Our comprehensive reports detail findings, risk levels, and actionable remediation steps, while providing continuous vulnerability management and prioritization guidance to strengthen your overall security posture.
What We Do?
Security Architecture
We conduct in-depth assessments of your security architecture, identifying vulnerabilities and recommending improvements. Our analysis covers network segmentation, access controls, cloud security, encryption, and identity management. We also evaluate incident response capabilities and guide the integration of emerging technologies. Our service provides actionable insights to enhance security, align with industry best practices, and ensure regulatory compliance while supporting business objectives.
Secure Code Review
Our secure code review or Static Application Security Testing (SAST) enhances the code security of your applications. Our approach includes both manual and automated code reviews to identify vulnerabilities and coding flaws. We assess security controls, data handling practices, and adherence to secure coding standards. Our team provides detailed reports highlighting issues and actionable remediation steps. By integrating secure coding practices into your development process, we help you build resilient applications that safeguard sensitive data and comply with industry regulations.
Cyber Security Strategy
Our comprehensive cyber security strategy involves assessing risks, threat modeling, and developing policies, standards and procedures to protect against vulnerabilities. Strategy is tailored to your organisation’s risk appetite. Strategy will incorporate penetration testing, and vulnerability assessments are used to identify and address weaknesses. Identity and Access Management (IAM) secures user authentication, while Endpoint Detection and Response (EDR) safeguards devices. Business Continuity Planning (BCP) and Disaster Recovery (DR) ensure operational resilience. Examples include securing cloud infrastructure with Zero Trust models and conducting phishing simulations to enhance security posture.
Risk Management and Governance
Our Risk Management services include identifying, analyzing, treating, and monitoring risks, through asset inventory, vulnerability assessments, implementing controls, and continuous monitoring. Our Governance services focus on aligning security with your business goals, developing robust policies, ensuring compliance, and establishing decision-making frameworks. We also help build a strong security culture and drive continuous improvement.
Business Continuity & Disaster Recovery (BC/DR)
Our tailored Business Continuity & Disaster Recovery (BC/DR) services to ensure resilience against disruptions. We provide risk assessments, backup and recovery planning, high-availability solutions, and disaster recovery strategies. Our services include crisis management, incident response, and regular DR testing to minimize downtime. With effective failover mechanisms and real-time monitoring, we help businesses safeguard critical data, maintain operations, and recover swiftly from cyber incidents or unforeseen disruptions.
Security Awareness & Training
Our security Awareness and Training services to strengthens your organisation’s defense against cyber threats. We provide training on cyber hygiene, phishing awareness, secure coding practices, and compliance requirements like GDPR and PCI DSS. Our programs include simulated phishing exercises, hands-on secure development training, and executive-level cybersecurity awareness. By educating employees on threat identification and best practices, we help organizations reduce risks, enhance security culture, and ensure regulatory compliance.
Compliance & Regulatory Support
Compliance & Regulatory services help businesses meet industry standards like GDPR, ISO 27001, PCI DSS, NIST, and SOC 2. Our services include security audits, gap analysis, and readiness assessments to identify compliance risks. We also offer vendor and third-party risk management to ensure supply chain security. By aligning security controls with regulatory requirements, we help organizations achieve compliance, reduce risks, and maintain trust with customers and stakeholders.
Privacy By Design
Privacy by Design Services integrates privacy protection into your organization’s foundation. We conduct privacy impact assessments, implement data minimisation strategies, and design user-focused privacy controls. Our approach includes end-to-end security measures, privacy-preserving data architectures, and clear, transparent policies supported by advanced technologies. We also establish strong data retention and deletion protocols, provide staff training on best practices, and conduct regular audits to ensure ongoing compliance with evolving regulations.
Security By Design
We embed security early in the software development lifecycle, minimising vulnerabilities while aligning with IT and business objectives. Our services include threat modelling, architecture and design reviews, and vulnerability assessments. By incorporating industry security standards, we strengthen application security from design to deployment. We help businesses integrate security into DevOps tools and workflows, automating compliance through Continuous Delivery (CD). Our solutions include static code analysis, dynamic vulnerability scanning, and third-party security tool integration in CI/CD pipelines.
Red Team, Blue Team
Our Red Team and Blue Team exercise offers a comprehensive approach to cybersecurity. The Red Team simulates real-world cyberattacks to identify vulnerabilities, while the Blue Team focuses on detecting, responding to, and mitigating threats. Key activities include penetration testing, threat hunting, incident response drills, and evaluating security controls. This collaborative exercise enhances detection capabilities and improves response strategies. Our service provides actionable insights to strengthen your defenses, ensuring resilience against evolving cyber threats and safeguarding critical assets.
Penetration Testing and Vulnerability Assessment
Our expert team conducts Penetration Testing and Vulnerability Assessments to identify weaknesses in your infrastructure, applications, and processes. We simulate real-world cyberattacks through thorough scans and manual testing, assessing the potential impact of discovered vulnerabilities. Key activities include network penetration testing, web application assessments, social engineering simulations, and cloud infrastructure evaluations. Our comprehensive reports detail findings, risk levels, and actionable remediation steps, while providing continuous vulnerability management and prioritization guidance to strengthen your overall security posture.
Team Certifications
Our security researchers and assessors are fully qualified. The security researchers are recognised by leading bug bounty programmes, run by the most well-known names in the technology industry.
















Technology Stack

CI/CD
Jenkins, Maven, Whitesource, Go CD, Bamboo, GitLab CI, CircleCI, Travis CI, Docker, Kubernetes, Terraform

Architecture
Microsoft SDL Threat Modeling Tool, Irius Risk, OWASP, CWE/SANS, NIST SP 800-53, ISO 27001

Security Testing
Wireshark, Metasploit, Nessus, Aircrack, Snort, BackTrack, Netcat, Burp Suite, Invicti, Fortify, OWASP ZAP, Nikto
Insights
Why Replacing Developers with AI Is Going Wrong and What Smart Leaders Are Learning Instead?
AI has not removed engineering effort. It has relocated it. Time once spent writing code is now spent reviewing, debugging, securing and unpicking it. Organisations that rushed to replace developers with AI are discovering that they have traded clear headcount savings for hidden technical debt, fragile systems and a greater dependence on their most experienced engineers. Vibe coding with AI can be powerful for proofs of concept and investor friendly demos, but only when the code is treated as disposable experiment tooling rather than the foundation of a production platform. The organisations pulling ahead are not asking how to replace developers with AI. They are asking how to combine machine speed with human judgement, using rapid AI powered experimentation at the edges and disciplined engineering at the core to build systems that are faster, safer and more resilient.
Digital ID: The Key to a Modern UK or a Threat to Our Freedom?
The debate around digital ID in the United Kingdom is intensifying. While some view it as an important step towards a modern and efficient society, others see it as a potential threat to privacy and individual freedom. The government’s proposed digital ID aims to simplify identity verification, reduce fraud and improve access to public services. Yet it also raises serious questions about data protection, inclusion and state control. Its success will depend on building trust through transparency, security by design and public engagement, ensuring that digital identity empowers citizens rather than limits them.
The Card Payments Industry at a Transformative Crossroads
Our latest insight highlights the key challenges shaping the future of the card payments industry. Those who do not keep pace with change will face significant obstacles ahead in sustaining their business.
Contact Us now for a Free Consultation
Reach out, and let’s create a universe of possibilities together!
Let’s connect