What is Security by Design?
Security by Design is an approach to application development that embeds security measures directly into the software from the earliest stages, rather than treating them as an afterthought. This proactive strategy involves integrating security considerations into the system requirements and architecture right from the beginning, ensuring that the applications are more resilient and less prone to breaches. The core idea is simple yet powerful: applications designed with security as a fundamental component are inherently more robust and capable of withstanding potential threats.
Why is Security by Design Important in the Software Development Lifecycle?
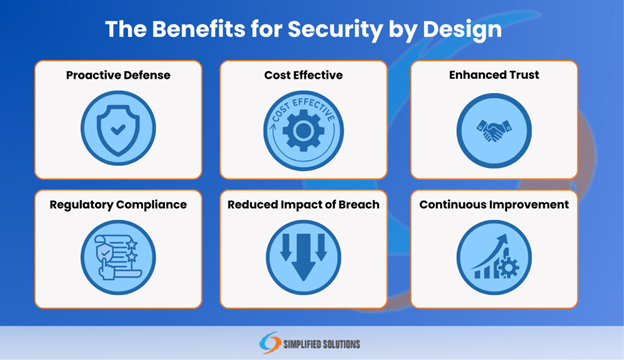
Shifting security to the left—addressing it early in the development process—is crucial for delivering secure software. Here are six key benefits:
Proactive Defense: By integrating security from the start, organizations establish defenses against potential threats before they materialize.
Cost-Effective: Identifying and mitigating security risks early in the design phase can save organizations significant costs associated with breaches.
Enhanced Trust: Applications developed with Security by Design principles earn greater trust from users, demonstrating a commitment to protecting their data.
Regulatory Compliance: Incorporating security measures from the outset simplifies compliance with regulatory requirements
Reduced Impact of Breaches: Even if a breach occurs, systems built with these principles are better equipped to limit damage and recover quickly.
Continuous Improvement: Security by Design fosters continuous monitoring and testing, allowing for the ongoing enhancement of system security.
The Journey of Security by Design
Historically, security was often an afterthought for many organizations. However, as the financial and reputational impacts of breaches became evident, this trend has shifted. Building secure applications from the ground up is now recognized as more cost-effective than dealing with the aftermath of a breach.
Security by Design can be built into two major categories: Process and Application Controls.

Processes
Security Standards, Metrics, and Governance: Establishing clear security standards, measurable metrics, and governance frameworks is crucial for ensuring ongoing compliance and improvement in security practices.
Requirement Management: Security requirements must be carefully defined and aligned with the organization’s overall security objectives, ensuring they are integrated into the project’s requirements from the beginning.
Impact Analysis: Understanding the critical assets and the organization’s risk appetite helps in assessing potential security threats and designing appropriate controls to mitigate risks.
Threat Modeling: Techniques like STRIDE and DREAD, among others, are used to identify and prioritize potential security threats based on their severity and impact.
Design Review: Regularly reviewing the application’s design helps identify potential vulnerabilities before implementation, ensuring security is integrated throughout.
Code Review: Automated tools and manual reviews by experienced developers help detect vulnerabilities and ensure adherence to security best practices.
Change Management: Careful control and documentation of changes ensure that updates do not introduce new vulnerabilities.
Training: Ongoing security training for developers and stakeholders is essential to maintain a high level of application security.
Application Controls
Auditing & Accountability: Implementing mechanisms to track and log changes ensures that unauthorized activities can be detected and investigated.
Zero Trust Architecture: This framework emphasizes strict access controls, data segmentation, continuous monitoring, and strong authentication to minimize risks.
Multi-Factor Authentication (MFA): MFA significantly reduces the risk of unauthorized access by requiring multiple forms of verification.
Secure Defaults: Ensuring that applications are configured with secure settings by default helps prevent vulnerabilities from misconfigurations.
Cryptography: Using strong cryptographic algorithms and secure key management practices is essential for protecting sensitive data.
Third-Party Libraries Vulnerability Assessment: Regular assessments of third-party libraries help identify and mitigate risks associated with outdated or vulnerable components.
Key Management: Secure storage and management of cryptographic keys are critical for maintaining data integrity and confidentiality.
Security Testing: Regular testing, including penetration testing and vulnerability scanning, helps identify and address security weaknesses before deployment.
Code Signing: Digitally signing application code ensures its integrity and authenticity, preventing the distribution of tampered or malicious code.
Security by Design and Regulatory Compliance
Security by Design helps organizations meet various regulatory and compliance requirements, including (but not limited to):
ISO 27001: Development controls, such as coding practices, are essential.
PCI DSS: Security by Design directly impacts compliance with several PCI DSS requirements.
NIS 2: Emphasizes robust supply chain security, cryptography, and multi-factor authentication.
GDPR: Requires auditing, change management, and secure handling of Personally Identifiable Information (PII).
Conclusion
Security by Design is critical for reducing security risks, financial losses, and reputational damage in the long term. As the threat landscape evolves with advancements in technology, including AI, it’s essential to embed security principles into the very fabric of application development. Remember, application security is an ongoing process, not a one-time exercise. Continuous attention is vital for maintaining a secure environment. Start building security in from the ground up, rather than bolting it on as an afterthought.
No single Security by Design approach fits all organizations. The process and controls must be tailored to factors such as the industry, application type, regulatory requirements, team skill set, risk tolerance, and budget. Contact Simplified Solutions experts to learn more.




