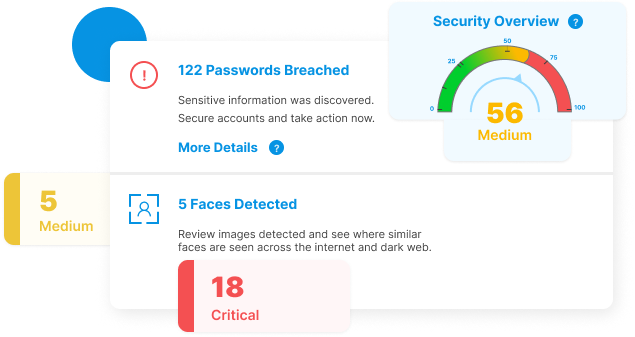
Proactive Application Security Penetration Testing
Penetration testing is a simulated cyberattack on a computer system or network that is performed by a security professional to identify and assess security vulnerabilities. Our security experts use the same tools and techniques as attackers